Emerging in early September 2025, the Yurei ransomware has swiftly drawn attention for its novel combination of Go-based execution and ChaCha20 encryption.
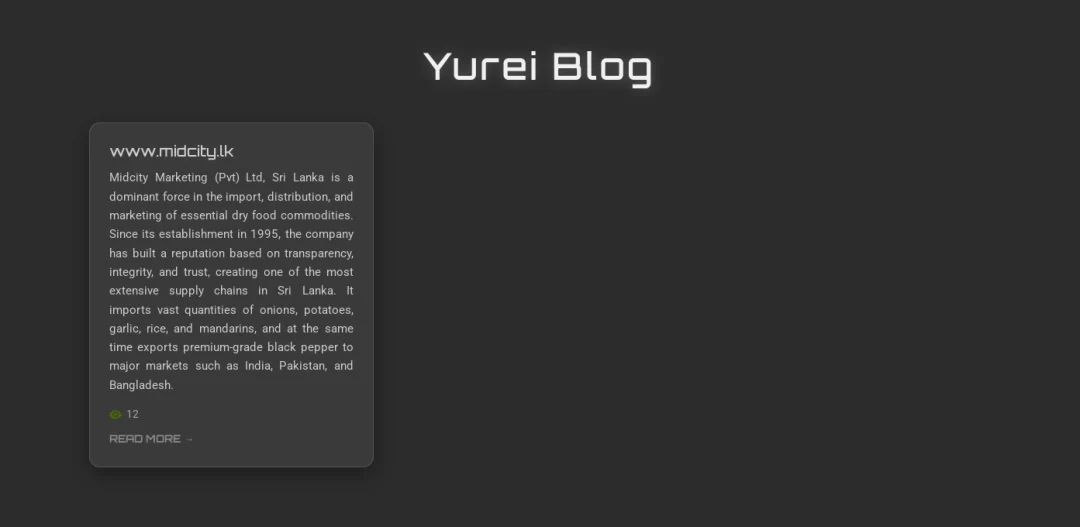
First documented on September 5 when a Sri Lankan food manufacturer fell victim, the threat actor behind Yurei adopted a double-extortion model: encrypting files while exfiltrating sensitive data for additional leverage.
Within days, two more victims in India and Nigeria were publicly listed, underscoring the operator’s rapid expansion.
Unlike many sophisticated groups that develop custom toolsets, Yurei’s codebase traces back to the open-source Prince-Ransomware project, raising questions about the skill level and resources of the attackers.
At its core, Yurei leverages Go’s concurrency features to enumerate all drives in parallel and encrypt files with the ChaCha20 algorithm.
For each file, a new random ChaCha20 key and nonce are generated, then encrypted using ECIES with the attacker’s public key.
The resulting ciphertext, key, and nonce are concatenated with delimiters:-
// Generate random key and nonce
key := generateChaCha20Key()
nonce := generateNonce()
// Encrypt file content
encryptedData := chaCha20Encrypt(content, key, nonce)
// Protect key and nonce with ECIES
protectedKey := eciesEncrypt(key, publicKey)
protectedNonce := eciesEncrypt(nonce, publicKey)
// Store encrypted file
store := protectedKey + "||" + protectedNonce + "||" + encryptedDataCheck Point researchers noted that Yurei retains symbols in the binary, a mistake inherited from the Prince-Ransomware builder, which did not strip debugging information.
This oversight provided analysts with clear function names such as Yurei_encryption_generateKey and Yurei_filewalker_EncryptAllDrivesAndNetwork, streamlining the reverse-engineering process.
Shadow Copy Recovery and Defensive Implications
Despite this, Yurei’s use of Go complicates detection for some legacy antivirus products, illustrating how language choice can impact defensive measures.
Following successful encryption, Yurei attempts to set a custom wallpaper via PowerShell, though the absence of a valid URL causes the command to fail, resulting in a blank background.
The embedded PowerShell snippet mirrors that of its Prince-Ransomware predecessor:-
(New-Object System.Net.WebClient).DownloadFile('<WallpaperURL>', "$env:TEMP\Wallpaper.png")
Add-Type -TypeDefinition @"
using System;
using System.Runtime.InteropServices;
public class Wallpaper {
[DllImport("user32.dll", CharSet=CharSet.Auto)]
public static extern bool SystemParametersInfo(int uAction, int uParam, string lpvParam, int fuWinIni);
}
"@
[Wallpaper]::SystemParametersInfo(20, 0, "$env:TEMP\Wallpaper.png", 3)
In the context of defensive strategies, Yurei’s failure to remove Volume Shadow Copies reveals a critical weakness.
Organizations with VSS enabled can recover files without paying ransom, although leaked data remains at risk.
The combination of rapid encryption, data exfiltration, and half-baked persistence techniques reflects a low-effort but effective operation.
As Yurei continues targeting diverse sectors, security teams are urged to monitor for the distinct file extension .Yurei, enforce strict egress controls, and validate VSS snapshots to mitigate the impact of this emerging threat.
