Security researchers have uncovered a sophisticated malware campaign spanning seven years, where threat actors behind AppSuite-PDF and PDF Editor applications systematically abused code-signing certificates to legitimize their malicious software.
The actors, tracked under the malware family name BaoLoader, have utilized at least 26 code-signing certificates obtained through fraudulent business registrations, primarily targeting users seeking PDF editing tools and productivity applications.
The campaign demonstrates a calculated approach to certificate authority manipulation, with threat actors establishing legitimate businesses across multiple jurisdictions including Panama, Malaysia, and the United States.

These entities served as fronts for obtaining code-signing certificates from major certificate authorities including SSL.com, GlobalSign, DigiCert, and Sectigo.
The malware has been distributed under various guises, including AppSuite-PDF, PDF Editor, ManualFinder, PDFTools, PDFProSuite, and OneStart, often masquerading as potentially unwanted programs (PUPs) while harboring backdoor capabilities.
What sets this campaign apart from typical certificate abuse scenarios is the actors’ consistent pattern of obtaining multiple certificates for identical company names from different certificate authorities.
Expel researchers identified this unusual behavior while analyzing the CertCentral.org database, noting that among over 1,500 documented organizations with abused certificates, these actors were unique in their geographic certificate patterns and systematic approach to legitimacy simulation.
The threat actors’ methodology extends beyond simple certificate procurement to include sophisticated distribution mechanisms.
Files have been uploaded to platforms like VirusTotal under numerous deceptive names, with single executables appearing as “ZoomSetup,” “WinRarSetup,” “MinecraftSetup,” and various PDF-related applications.
This multi-naming strategy indicates deliberate attempts to maximize infection vectors by appealing to diverse user interests and needs.
Certificate Authority Exploitation and Business Registration Patterns
The technical infrastructure behind BaoLoader reveals meticulous planning in certificate acquisition strategies.
The actors established companies with media-focused naming conventions, including GLINT SOFTWARE SDN. BHD., ECHO INFINI SDN. BHD., Summit Nexus Holdings LLC, Apollo Technologies Inc., and Caerus Media LLC.
Each entity was registered with legitimate business documentation, enabling the actors to pass initial certificate authority verification processes.
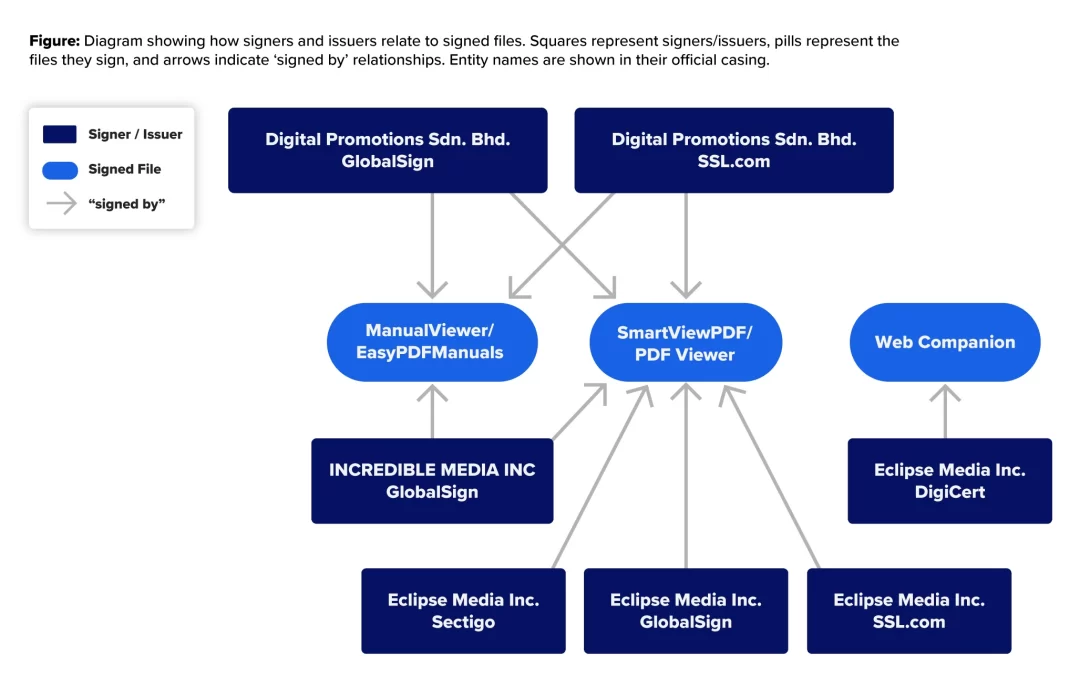
Analysis of the certificate metadata reveals consistent business serial numbers across multiple certificate authorities for identical company names.
For instance, Eclipse Media Inc. certificates were issued by GlobalSign, SSL.com, Sectigo, and DigiCert, all containing matching business registration identifiers.
This approach allowed the actors to maintain operational continuity when individual certificates faced revocation, seamlessly transitioning between certificate authorities while maintaining the same organizational identity.
The malware’s persistence mechanisms include PowerShell execution designed to load Web Companion components, executing commands that bypass execution policies and load assemblies from encrypted files.
The campaign’s evolution from simple adware distribution to backdoor deployment represents a concerning escalation in threat actor capabilities, demonstrating how certificate abuse can provide extended operational longevity for malicious campaigns targeting productivity software users.
